"How to Protect Your Website from SQL Injection"
SQL injection is a major security vulnerability that allows attackers to manipulate a website’s database queries, potentially exposing sensitive data or causing damage. Despite being a well-known threat, it continues to affect many web applications. In this blog, we'll dive into how SQL injection works, its impact, and most importantly, how to protect your web applications from this common attack. Whether you're a developer or just curious about web security, this blog will help you understand the risks and solutions surrounding SQL injection.
What is SQL Injection?
SQL Injection (SQLi) is one of the most common and dangerous cybersecurity vulnerabilities that can compromise a website's or web application's security. It occurs when an attacker exploits an insecure application by injecting malicious SQL code into input fields that interact with a database. This enables the attacker to manipulate the database in unauthorized ways, often leading to data breaches, loss of sensitive information, and complete server compromise.
SQL Injection happens when user input is not properly sanitized before being passed to an SQL query. Since SQL commands can manipulate databases, attackers can use this flaw to execute harmful commands, read sensitive data, delete records, or even take control of the database and application.
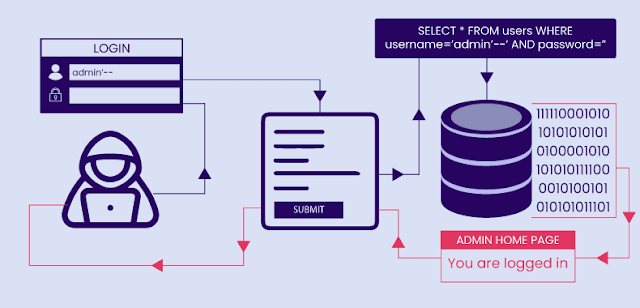
How SQL Injection works
To understand SQL Injection, it’s helpful to know how a basic SQL query functions. A typical SQL query that fetches user data might look like this:
In a secure scenario, the user_input would be sanitized to prevent any malicious code from altering the structure of the query. However, in vulnerable applications, an attacker could manipulate this query by inserting special characters or code, like:
This would result in the SQL query being executed as:
Because '1' = '1' is always true, the query will return all user records, potentially exposing sensitive information like usernames, passwords, and other personal data.
Common Types of SQL Injection Attacks
1. In-Band SQL Injection: In this type, the attacker can directly view the results of the injected query. This is the most common form of SQLi and can easily lead to data exposure.
3. Out-of-Band SQL Injection: This occurs when the attacker cannot get the results directly from the same connection. Instead, the attacker relies on external servers to send the data or create some side effects, such as sending DNS requests or making HTTP requests to external resources.
4. Union-based SQL Injection: This method allows the attacker to combine results from multiple SQL queries into a single response, leading to the disclosure of more information from the database.
How SQL Injection Can Be Exploited
SQL Injection attacks can have disastrous consequences. Here are some examples of how attackers can exploit SQLi vulnerabilities:
- Data Breach: Attackers can view and extract sensitive data such as user credentials, payment information, or personal records.
- Data Manipulation: Malicious users can delete, update, or add records in the database, potentially causing the application to malfunction or lose valuable data.
- Authentication Bypass: Attackers can use SQL Injection to bypass login pages and gain unauthorized access to user accounts or administrative panels.
- Privilege Escalation: With the right SQL commands, attackers can elevate their privileges and gain control of the server, allowing them to execute system-level commands.
- Denial of Service (DoS): By injecting large numbers of queries or malformed input, attackers can overwhelm a database, leading to service disruptions or crashes.
How to Prevent SQL Injection
Preventing SQL Injection is crucial for safeguarding your website and database from attacks. Here are some simple yet effective prevention techniques:
- Use Prepared Statements (Parameterized Queries): The most effective way to prevent SQLi is to use prepared statements with parameterized queries. Prepared statements separate the SQL logic from the data, preventing attackers from injecting malicious code.
Here’s an example in PHP:
$stmt = $conn->prepare("SELECT * FROM users WHERE username = ? AND password = ?");
$stmt->bind_param("ss", $username, $password);
$stmt->execute();
- Employ Stored Procedures: Stored procedures can help limit direct access to SQL queries and avoid the risk of injection. However, stored procedures must also be properly written and parameterized to avoid vulnerabilities.
- Validate User: Input Always validate and sanitize user input to ensure that it adheres to the expected format. For example, ensure that numeric fields only accept numbers and string inputs are properly escaped or filtered.
- Use ORM (Object-Relational Mapping): Libraries Many modern web frameworks come with ORM libraries (e.g., Django, Laravel) that abstract raw SQL queries and automatically handle input sanitization, making it harder for attackers to exploit vulnerabilities.
- Limit Database Permissions: Make sure that your database user accounts have the minimum privileges required for their tasks. For instance, a web application account should only have read and write permissions but should not have administrative access.
- Error Handling and Reporting: Never display detailed error messages to end users, as they can provide clues to attackers about the underlying database structure. Instead, use generic error messages and log detailed errors for internal use only.
- Regular Security Audits: Regularly audit your codebase, perform vulnerability scanning, and conduct penetration testing to identify potential SQL Injection vulnerabilities before attackers do.
SQL Injection remains one of the most common and dangerous security threats facing websites and web applications. By understanding how SQLi works and implementing strong preventive measures, you can significantly reduce the risk of SQL Injection attacks on your systems. Always prioritize secure coding practices, validate user input, and regularly test your applications for vulnerabilities to ensure your users' data is safe.