"Kali Linux is not just an Operating System, but it is the real Gem of Computer Science".
For Ethical hackers, Penetration testers, and security experts alike, Kali Linux has become a potent tool. With its wide toolkit and emphasis on security, Kali Linux has emerged as a crucial tool for both individuals and businesses looking to safeguard their digital assets. We will delve into the realm of Kali Linux in this blog article, looking at its features, uses, and advantages for cybersecurity aficionados. This article attempts to provide you a firm grasp of Kali Linux and its potential, whether you're a novice or a seasoned professional.
What is Kali Linux ?
Kali Linux, based on Debian Linux, is a specialized operating system designed for penetration testing and digital forensics. It comes pre-packaged with a wide range of security tools, making it an all-in-one solution for cybersecurity professionals. Kali Linux offers an environment specifically crafted to support ethical hacking activities, including vulnerability assessment, network analysis, password cracking, and more. Its popularity can be attributed to its user-friendly interface and a robust collection of open-source tools.
 |
What do you understand by Kali Linux? |
Key Features and Tools :
Its extensive selection of security tools is one of Kali Linux's distinguishing qualities. The package includes, among other things, tools for network scanning, post-exploitation, and reconnaissance. The list of effective tools at your disposal includes Metasploit Framework, Nmap, Wireshark, Aircracking, and John the Ripper, to name just a few. Kali Linux also offers a setting for incident response and digital forensics. Investigators can examine and retrieve data from compromised systems using tools like Autopsy, Foremost, and Volatility. For cybersecurity experts engaged in incident response and forensic investigations, Kali Linux becomes a crucial tool.
 |
Key Features and Tools Kali Linux |
Practical Applications :
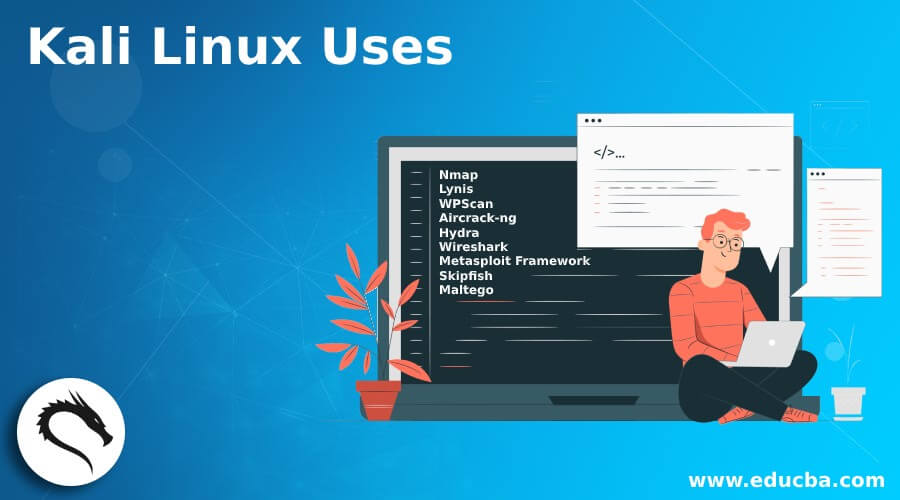 |
Practical Applications of Kali Linux |
Benefits and Limitations :
Numerous advantages of Kali Linux include its extensive toolkit, frequent upgrades, and community support. Users of different levels of competence can utilize it thanks to its simple user interface. Because Kali Linux is open-source, it promotes collaboration and may be tailored to meet certain requirements. But it's important to be aware of Kali Linux's possible shortcomings. Beginners may find its broad toolkit intimidating and will need to learn how to use it properly. The potent tools of Kali Linux should only be used for morally and legally correct activities as they have the potential to be abused in the wrong hands.
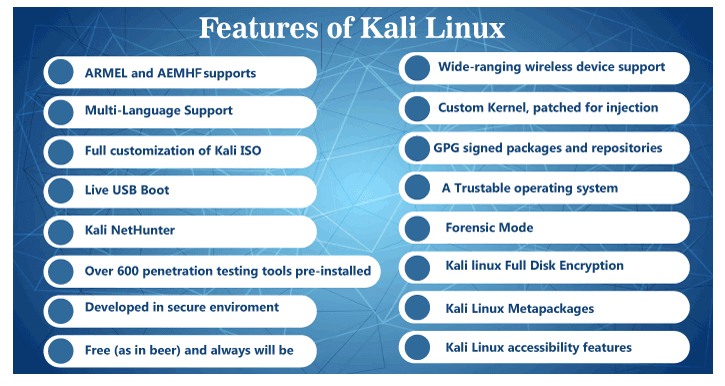 |
Features of Kali Linux |
