From Fiction to Reality: "Understanding the Pegasus Virus and its Implications".
The idea of privacy has gained prominence in international discussions in an era dominated by technology breakthroughs. Protecting personal privacy has become crucial due to the quick development of digital communication and the enormous variety of information shared online. However, the Pegasus virus's appearance has brought up serious issues regarding the erosion of digital privacy and the possibility of never-before-seen risks in this connected world. The Pegasus virus is a potent and sophisticated cyber spying instrument that has sprung from fiction and into actual fact, reverberating throughout the whole digital community. This essay explores how the Pegasus virus went from being a hypothetical idea to a real threat while analyzing its effects on security, privacy, and society as a whole.
Understanding the Pegasus Virus: "A Closer Look"
The Pegasus virus, developed by the Israeli cyber intelligence firm NSO Group, represents the epitome of sophisticated surveillance technology. Initially conceived as a tool to combat criminal activities and terrorism, it has evolved into a powerful weapon capable of infiltrating smartphones, exploiting vulnerabilities, and gaining access to sensitive data. Pegasus has brought to life what was previously the stuff of spy novels, making surveillance a skill that can be acquired by both state and non-state actors. The Pegasus virus was previously a fiction invention, a narrative device that appeared like a far-off possibility, named after the fabled winged horse. The world has just been shocked into realizing the existence of this sophisticated cyber espionage tool, nevertheless, as a result of recent discoveries.
"Functioning and Capabilites"
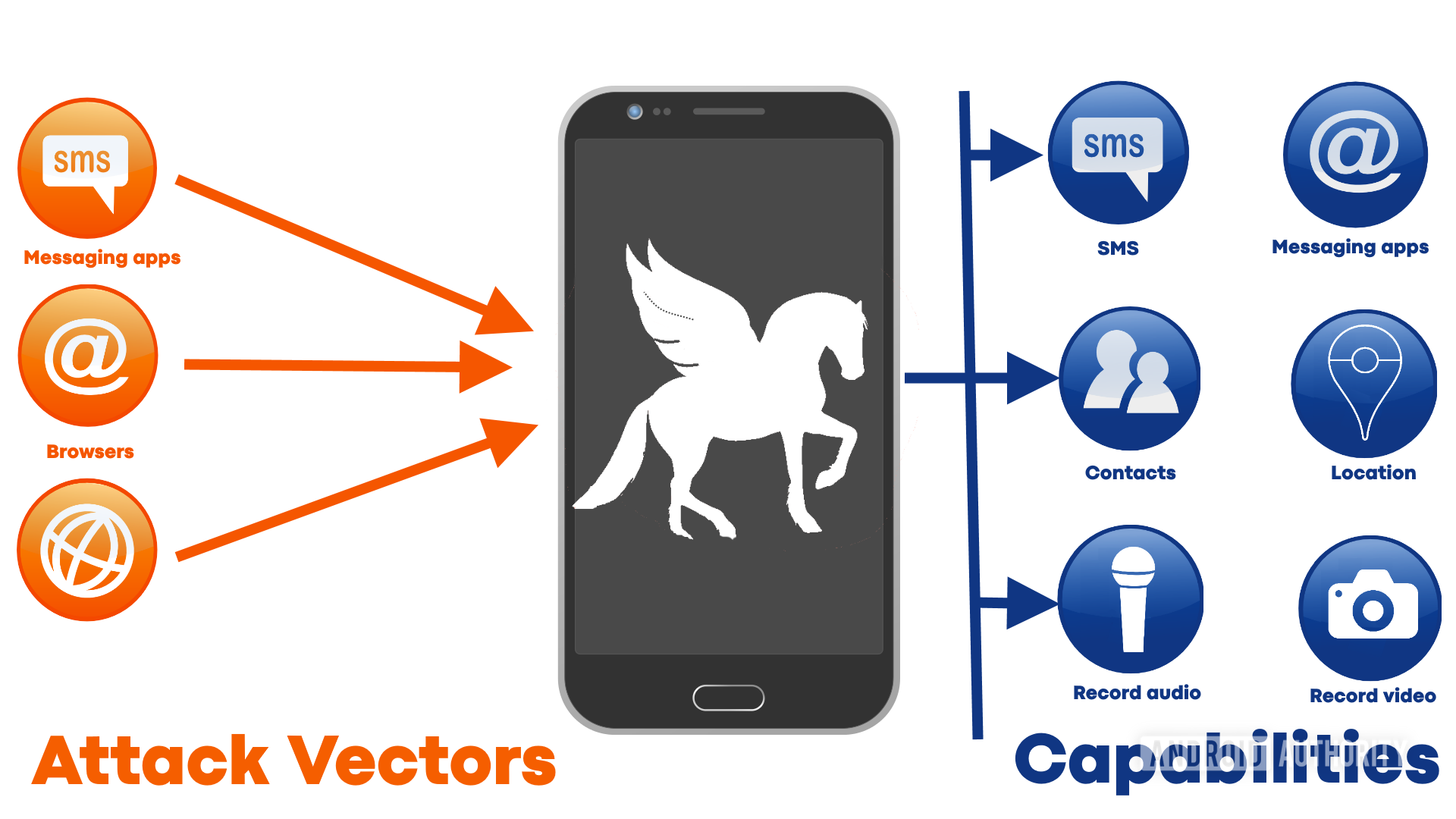
At its core, the Pegasus virus functions as spyware that takes use of recently discovered flaws in widely used mobile operating systems like iOS and Android. Its stealthy and very successful infiltration procedure frequently necessitates no user interaction. Pegasus may access a wide range of personal information, including texts, calls, emails, and even location information, once it has been installed on a device. It has the ability to transform the gadget into a powerful instrument for remote surveillance by turning on the camera and microphone without the user's awareness. Pegasus may access a wide range of personal information, including texts, calls, emails, and even location information, once it has been installed on a device. It can activate the device's camera and microphone without the user's knowledge, turning the device into a potent tool for remote surveillance. Pegasus' flexibility is evidence of how cyber threats are constantly changing. It has proven to be capable of exploiting zero-day vulnerabilities, which are flaws in software that the vendor is unaware of and for which there are no patches available. .
The adaptability of Pegasus is a testament to the ever-evolving landscape of cyber threats. It has demonstrated the ability to exploit zero-day vulnerabilities, which are software vulnerabilities that are unknown to the software vendor and, thus, lack patches. This unique capability enables Pegasus to remain hidden from antivirus and security tools, making detection and prevention exceedingly difficult.
The Multifaceted and Far-reaching "Ramifications of Pegasus"
Its powers directly threaten personal security and privacy at the individual level. It is difficult for citizens, activists, journalists, and dissidents to express themselves freely and participate in vital dialogues without fear of retaliation because of extensive surveillance. It is impossible to overstate the impact on human rights and freedom of speech. It is impossible to overstate the impact on human rights and freedom of speech.
The Pegasus virus emphasizes the wider issues of the digital age from a societal standpoint. The ethics of surveillance, permission, and data ownership are critical issues as governments and corporations accumulate enormous amounts of data. A global discussion on the limits of monitoring in a democratic society has been sparked by the growth of cyber espionage technologies like Pegasus, which raises questions about the harmony between individual rights and national security goals.
The "Struggle" between Privacy and Security
The emergence of the Pegasus virus highlights the complex interplay between security and privacy. While its capabilities can aid in preventing criminal activities and terrorist threats, the methods it employs are inherently invasive. The essence of contemporary cybersecurity discourse is this conflict between protecting the public and maintaining individual privacy. Striking the right balance requires collaborative efforts from governments, tech companies, and civil society to establish regulatory frameworks that ensure responsible and transparent use of such technologies.
Geopolitically, the emergence of the Pegasus virus has reshaped the dynamics of international relations. The revelation that several governments have used this tool to target journalists, activists, and political opponents highlights the potential for diplomatic tensions and mistrust among nations. State-sponsored cyber attack allegations could result in diplomatic problems, financial penalties, or even military retaliation. The idea of war has changed from the physical battlefield to the digital one, where the effects can be less obvious at first but can be just as damaging.
Strengthening Cybersecurity Measures: "The Evolution"
The Pegasus virus has reemphasized the significance of protecting against cyber-attacks. The transition from fiction to reality underscores the urgency for nations, corporations, and individuals to enhance their cybersecurity measures. This includes strengthening encryption protocols, implementing multi-factor authentication, and educating users about the risks of clicking on suspicious links or downloading unverified apps. As the Pegasus virus demonstrates, the potential for compromise is not limited to specific demographics; it spans across social, economic, and political strata.
To mitigate the implications of the Pegasus virus and its counterparts, a multi-pronged approach is imperative. First and foremost, software developers must prioritize robust security practices and rapid response to vulnerabilities. Regular updates and patches can minimize the risk of exploitation by zero-day vulnerabilities. Additionally, individuals need to be proactive about their digital hygiene, practicing caution while clicking on links, downloading apps, and granting permissions to applications. On a larger scale, governments must collaborate internationally to establish norms and regulations for cyber activities, ensuring that surveillance tools are used solely for legitimate purposes and in adherence to international human rights standards. Enhanced transparency and oversight mechanisms can help prevent misuse and protect individual rights.
The Virus underscores the urgent need to address the complex ethical, legal, and technical challenges that arise from the proliferation of advanced cyber espionage tools. Striking a delicate balance between security and privacy requires a concerted effort from all stakeholders, as we navigate the uncharted waters of the digital age. Only through collective action, we ensure that our technological advancements remain a force for good, rather than a tool for oppression and intrusion.