"Explaining how cryptography is used to protect data, authenticate users, and ensure the integrity of information in cybersecurity."
There has never been a greater need for strong cybersecurity measures, particularly in the connected digital world of today, where information is shared instantly and cyber threats are present everywhere. Cryptography and encryption form the cornerstone of modern cybersecurity and are at the core of this protection strategy. This blog explores the critical functions of cryptography and encryption in protecting private information, preventing online fraud, and maintaining the integrity of digital communications.
"Understanding Cryptography and Encryption"
The word Cryptography comes from the Greek words "kryptos," which means hidden and "graphein," which means to write. It is the study of safe communication when dealing with other parties, or adversaries, in public. It includes a range of methods and mathematical formulas designed to encode data so that unapproved parties are unable to decode it.
The process of converting readable plaintext data into unreadable ciphertext using an encryption algorithm and a cryptographic key is known as Encryption, and it is a basic idea in cryptography. Only those with the appropriate decryption key who are permitted can decode this ciphertext back into plaintext.
 |
Understanding Cryptography and Encryption |
"The Role of Encryption in Cybersecurity: Why is Encryption Essential?"
In the digital age, where information is currency, protecting it from unauthorized access is paramount. This is where encryption, the fundamental technique of contemporary cybersecurity, comes into play. Encryption is the act of turning readable data into an unreadable form. It protects sensitive data, including financial records, intellectual property, and personal information, by acting as a digital shield. The data is rendered unreadable to anyone lacking the required decryption key utilizing intricate algorithms and cryptographic keys.
To guarantee data confidentiality, integrity, and authenticity on a variety of digital platforms and communication channels, encryption is a highly effective instrument. Encryption improves cybersecurity protection in the following ways:
1. Data Breaches: Unfortunately, data breaches are becoming more frequent as cyberattacks are becoming more prevalent. Even if attackers can get past passwords and firewalls, encryption serves as a last layer of protection. Slightly minimizing the possible consequence of a breach, even if they get to obtain the encrypted data, it becomes extremely difficult to decode it without the key.
2. Privacy Protection: In an era where data privacy concerns are at an all-time high, encryption empowers individuals and organizations to maintain control over their sensitive information. By encrypting personal details like emails, medical records, and financial transactions, individuals can ensure that only authorized parties can access and process this data.
3. Compliance Requirements: Many industries, such as healthcare and finance, are subject to strict regulatory compliance requirements regarding data security. Encryption plays a crucial role in demonstrating adherence to these regulations, as it safeguards sensitive data entrusted to these organizations.
4. Authentication: In digital transactions, encryption is essential for confirming the identity of users and other entities. It makes use of methods such as public-key cryptography to facilitate key exchange and safe authentication.
5. Secure Communication Channels: By encrypting data while it is in transit, encryption protects communication channels including email, instant messaging, and web browsing. This stops third parties from listening into conversations and executing man-in-the-middle attacks.
 |
Role of Encryption in Cyber Security |
"Working of Encryption: How does Encryption Work?"
1. Algorithms: These are sophisticated mathematical formulas that control how data is converted from plaintext, which is its original format, to ciphertext, which is unreadable. The degrees of security provided by various algorithms vary, and each has advantages and disadvantages of its own.
2. Keys: Digital sequences known as "keys" serve as "passwords" for encryption and decryption. Symmetric keys, which are utilized for both encryption and decryption and asymmetric keys, which employ separate keys for encryption and decryption, are the two basic categories of keys. Selecting the right kind of key and keeping them safe are essential components of efficient encryption.
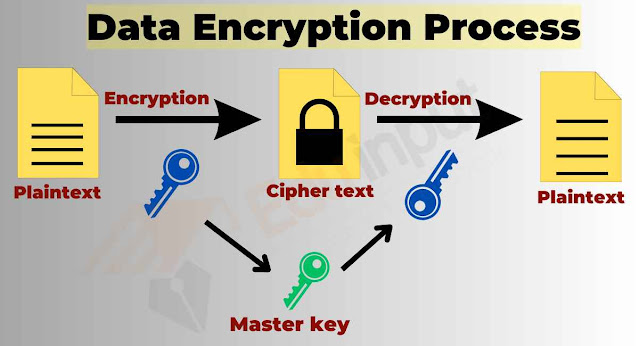 |
Working of Encryption Technique |
"Different types of Encryption"
Encryption techniques can be broadly categorized into two main types: symmetric encryption and asymmetric encryption.
1. Symmetric Encryption: In symmetric encryption, the encryption and decryption processes use the same key. The Advanced Encryption Standard (AES) and the Data Encryption Standard (DES) are two well-known symmetric encryption methods.
3. Asymmetric Encryption: Asymmetric encryption utilizes a pair of keys - a public key for encryption and a private key for decryption. This enables secure communication between parties without the need to share a secret key beforehand. Common asymmetric encryption algorithms include RSA and Elliptic Curve Cryptography (ECC).
 |
Types of Encryption |
"Challenges and Considerations: Implementing Effective Encryption"
1. Key Management: To guarantee the security of encrypted data, effective key management is essential. This entails creating, storing, distributing, and securely removing cryptographic keys.
2. Performance Overhead: In circumstances with limited resources, encryption and decryption procedures may result in a computational cost that affects system performance.
3. Regulatory Compliance: Adherence to data protection laws like GDPR, HIPAA, and PCI DSS demands that encryption specifications and deployment techniques be carefully planned.
 |
Challenges in Encryption Techniques |
